The threat from phishing continues to rise at an alarming pace. I will provide a few phishing emails I have saved and will be presented here as examples, but first – What is “Phishing”?
According to SANS.org, phishing is, “a type of attack that uses email or a messaging service to fool you into taking an action you should not take, such as clicking on a malicious link, sharing your password, or opening an infected email attachment. “(Dudley, 2018). Those who attempt to use phishing for a cyberattack are getting much better at convincing the victims that their messages are authentic. It would be very easy for someone to fall for one of these attacks.
A phishing email or message will usually portray some type of an emergency or urgency to make the reader feel that they need to act – NOW! Examples include: “Urgent: Someone has accessed your account – Change your password now”, offering something that is too good to be true (Dear Martha passed away and has no one to leave her $24, 347, 212.00 to so it’s yours if you’ll just…), messages that are from someone you know but the message doesn’t seem right (something your friend wouldn’t normally send), or messages that just seem off in some way (see examples below). These cybercriminals also use events to convince someone to react such as Hurricane Ian.
The phishing message that is received can invite you (or urge you) to visit a website. This could send you to a site that looks familiar (Paypal for example) that you must log into (they will generally urge you to change your password, etc – see below examples). If you do this (I have) it won’t take you anywhere (like to your Paypal account). However, they now have your username and password to your Paypal account and can log on to that account, change the password, and have ready access to everything that you would be able to do from that account (request money, send money, pull money from the attached bank account or credit card you have setup there, etc). This holds true for any account you have online (Bank accounts, retirement accounts, shopping accounts, social media accounts, etc). What I have (unfortunately) learned is that it can take weeks to months to regain access to some of these accounts.
Some of these phishing attacks can contain files that look legitimate but contain a payload that, when opened, can install malware on your computer (Malware is the overarching term used for Viruses, Worms, Trojans, Ransomware, Rootkits, Keyloggers, Bots, and Spyware/adware).
This malware will either be designed to destroy data on your system, open a door so the attacker can gain access to your computer (sometimes unnoticed for months), or install ransomware to scare you into spending money so you can get back on your computer.
Some relevant phishing statistics:
According to the FBI’s Internet Crime Complaint Center (IC3), phishing is, by far, the most common attack performed by cybercriminals (2020).
An annual report from Bolster (2021) stated that there were 6.95 million new phishing and spam pages created in 2021 and that the top three industries targeted were technology, retail, and finance.
Some examples:
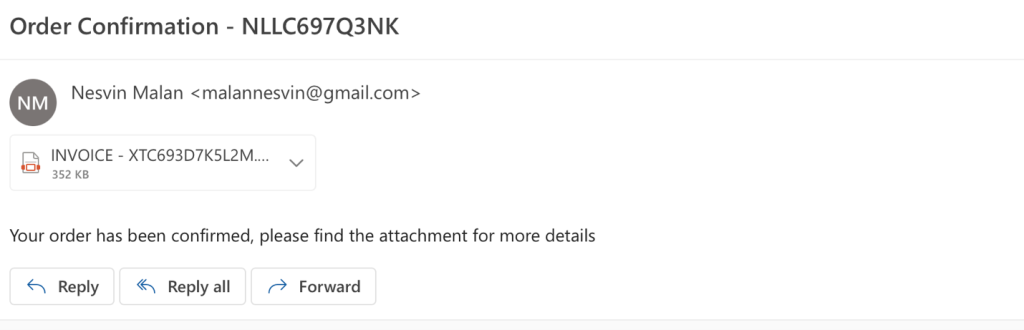
I don’t know who Nesvin Malan is – this is about an order from somewhere, but the email address is a Gmail account. All signs that something isn’t right. Here, if you click on the invoice (which is a .pdf file), there will probably be some type of unwanted action performed.
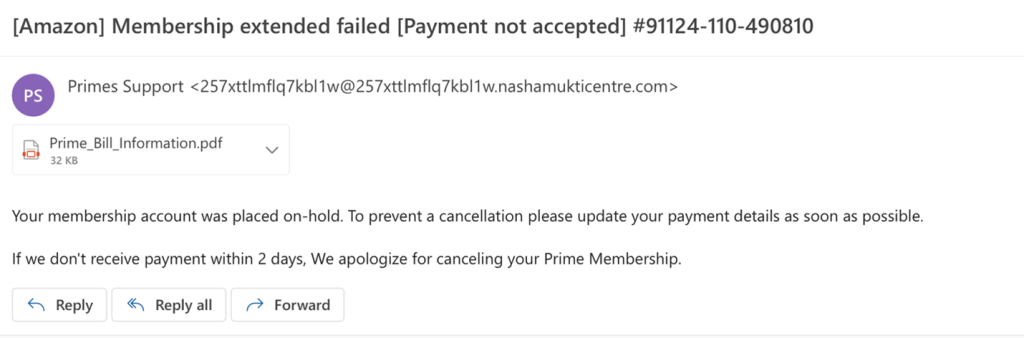
There are A LOT of people with an Amazon Prime Membership account. This one is marked as urgent and says that your Prime membership will be cancelled in 2 days if they don’t receive payment. Notice the unusual email address (if you don’t see the email address you can check the email properties). Again, there is a .pdf file that will probably cause harm to your system.
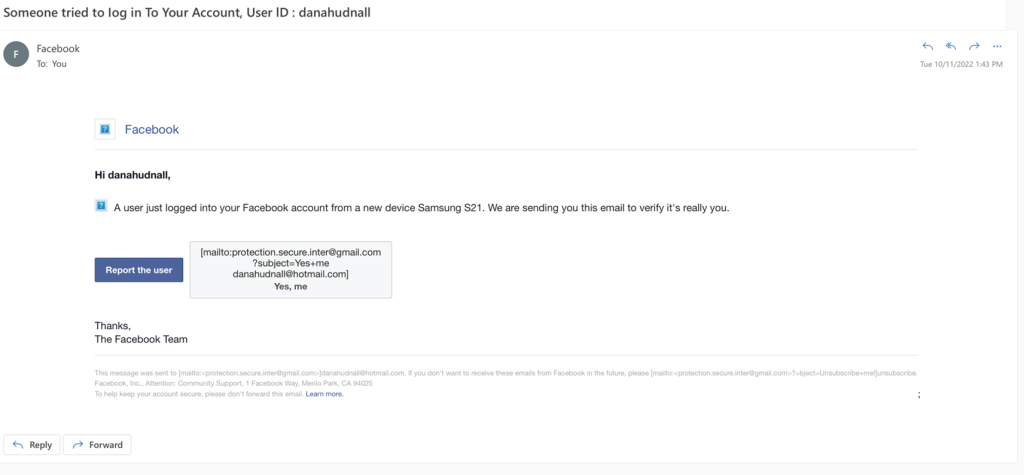
This is my favorite. I get this at least once a day. It’s urgent because “somebody tried to log in to my account” and I must report this user. There is actually no email address shown in the From line – you will either have to check the email properties or click “reply” (not recommended). It shows you what happens when you click the Report the User box to the right of that box – it doesn’t take you to a URL to report a user at all.
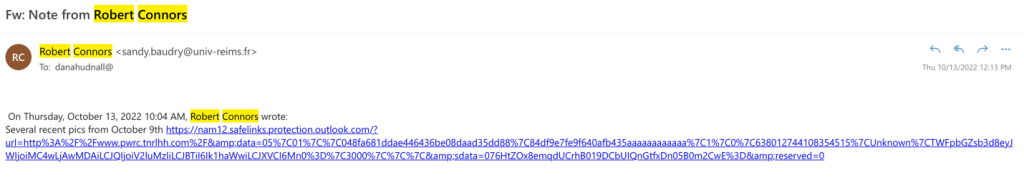
Bob Connors is a good friend of mine, but I know this is an impersonation email. – If you look at the email address, you’ll see something totally different from your friend’s email address. The tricky part here is that Bob often sends me links to music. If I wasn’t paying close attention, I might click on this link only to find that I’ve been had. I’ve received similar emails from other “friends” like this.

Here in Florida, quite a few people had their insurance cancelled (legitimately). This phisher took advantage of that and sent phishing emails out to spoof the recipient. Notice the email address (you’ll never receive a cancellation like this from a Hotmail account). The Cancellation Letter attachment sends you to a secure site (URL) that contains who knows what (I’m not trying it).
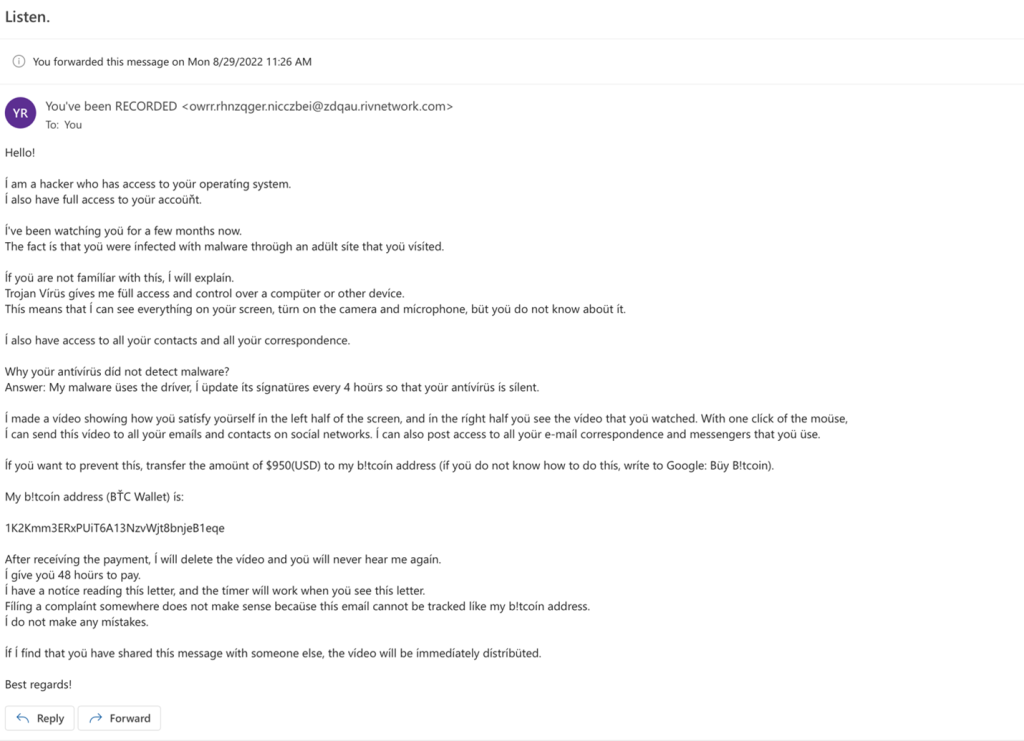
This is a halfway decent attempt at convincing the receiver that they need to send money, or they will be exposed. Notice the wording is a bit off.
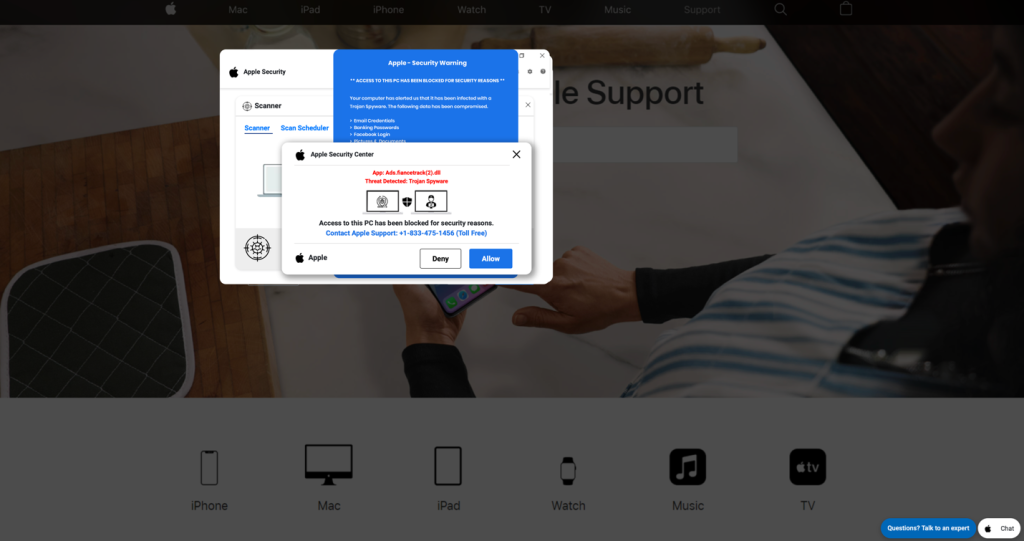
Another one of my favorites. It comes in Mac and Microsoft PC versions. This is a screenshot from my computer and has come up a few times now (in searches for information when clicking on URLs I shouldn’t have). These will make it appear that your computer has been locked (it’s not). There is generally a siren or blaring sound of some sort. This convinces a lot of people to call the number on the screen. When you call this number, you are told that the person on the other end needs to access your computer remotely and they attempt to get a credit card payment.
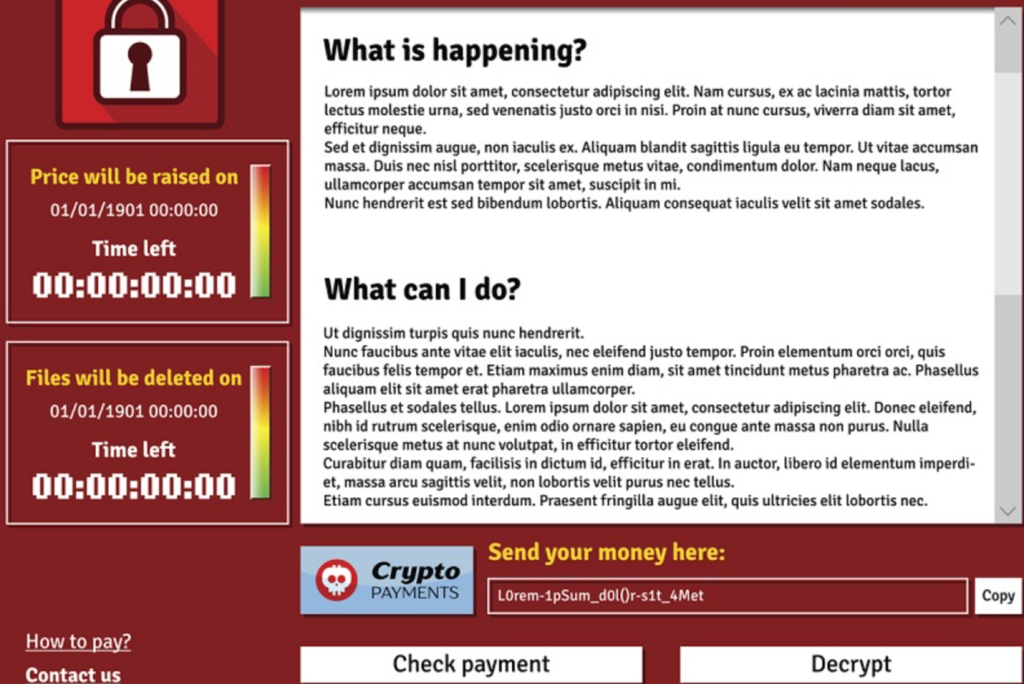
This is an example of what you might see in a ransomware attack. Although Cryptolocker (propagated through email) was one of the first “strains,” one of the most recent was the WannaCry attack. This scheme was propagated via an exploit called EternalBlue, which infected over 230,000 computer systems costing over $4B in financial losses. When this ransomware was discovered, the National Cybersecurity and Communications Integration Center urged users not to pay, to wipe systems clean, and restore from backup. Beware of future ransomware.
In summary, beware of emails and messages in general but, especially from someone you don’t know. Things to beware of are misspellings, urgency, a notice that your account is locked or a message that the sender has detected “suspicious activity,” a request to confirm personal or financial information, attachments from someone you don’t know/recognize (even if it looks like it’s someone you know or is someone you know – trust but verify), and links from someone you don’t know – even sometimes from someone you do know – see above). Finally, always look carefully at emails that are purportedly from an organization that you are affiliated with (Netflix, your bank, Amazon, your retirement fund, etc).
Even the most intelligent and competent people can fall for these phishing scams – as they grow in sophistication, you must stay vigilant. Think before you click!
Carlson, B (2021). Top cybersecurity statistics, trends, and facts. Retrieved from https://www.csoonline.com/article/3634869/top-cybersecurity-statistics-trends-and-facts.html
Dudley, T. (2018). Stop that Phish. Retrieved from https://www.sans.org/newsletters/ouch/stop-that-phish/
NCIIC (n.d.). What is WannaCry/WannaCrypt0r. Retrieved from https://www.cisa.gov/uscert/sites/default/files/FactSheets/NCCIC%20ICS_FactSheet_WannaCry_Ransomware_S508C.pdf